Your password manager’s master password secures your vault. It is essentially a key to unlock access to all of your other passwords. It would help if you always used a long, complex, and unique password. This is even more important for a password manager, though, given the sensitive information it protects. What is slightly less obvious is how your master password is used to generate an encryption key.
As with any website that securely stores passwords, Bitwarden hashes your password before storing the result in its database. This hashed value is used to authenticate you to the service and as an encryption key for your vault data. This process is the security standard because hashing algorithms are one-way functions. You can’t reverse the hashing process to determine the master password even if you know the hashed value.
The only attack that can be performed against a hashed password is a brute force attack where a hacker guesses the password until they end up with the result that matches. Additionally, as any minor change to the password generates an entirely different hashed result, there are no clues that your guess was close. Websites verify that you’ve entered the right password by checking the hash of the password you entered against the one in the database.
Why Change the Encryption Key Settings?
Bitwarden uses the hashing algorithm PBKDF2, which is specifically designed to hash passwords. One of its key features is that you can tune how many iterations the algorithm runs through. The number of iterations is a balancing game between the level of security needed and the processing power available.
It is recommended that the iteration count is tuned to take a quarter of a second on the weakest device you intend to use regularly. Originally, the recommended iteration count was 1000. Still, with processing power improvements in modern CPUs, the recommended iteration count is 100000 as of 2021. This number is designed not to take so long as to bother you, the user, but to be slow enough to restrict the performance of password guessing attacks severely.
Tip: Iteration count is a key feature of PBKDF2 as it can significantly slow down any brute force attempt. For example, with modern consumer computer components, it’s possible to make millions of guesses per second using many older hashing algorithms such as MD5.
With PBKDF2 correctly tuned, you can cut this down to the low thousands or even to the hundreds of guesses per second. This makes it a lot harder to perform a brute force attack that relies on making as many guesses as possible.
Bitwarden defaults to running the recommended 100000 iterations on your device and then an extra 100000 when your data reaches its servers. While you can’t configure the number of server-side iterations, you can change the number of client-side ones.
If your computer is ancient and slow and unlocking your vault regularly takes a long time, you may want to look into reducing the iteration count. Conversely, if you’re only using fast and modern devices, you may want to raise the iteration count for increased security.
How to Change Your Encryption Key Settings
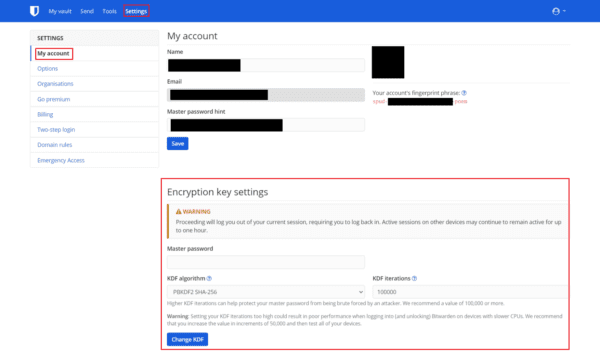
To be able to change your encryption key settings, you need to use the Bitwarden web vault. Switch to the “Settings” tab. Scroll down to the “Encryption key settings” section, then read all of the associated warnings. Next, enter your master password to verify account ownership. The “KDF algorithm” dropdown box allows you to choose which variant of PBKDF2 you want to use. Only one option is currently available, however, “PBKDF2 SHA-256”.
Tip: KDF stands for Key Derivation Function, while the PB at the start of PBKDF2 stands for Password-Based. KDF is another name for a hash function.
The only setting you can actually change here is the iteration count. It would help if you tuned this for the weakest device you plan to use to access your vault regularly. For example, you could tune it to take half a second on a powerful PC. It could then take ten seconds to unlock your vault on your less powerful phone if you did so. This will get annoying when it happens every time you want to access it.
Once you’ve selected several iterations, click “Change KDF.” This will log you out of your current session and expire all of your other sessions. However, it can take up to an hour to take effect on other devices. You should manually log out of all other sessions as soon as possible and then log back in. Making changes to your vault with an old encryption key can corrupt your entire vault, so play safe.
Conclusion
If you want to configure your security as much as possible, you can edit your encryption key settings. One option Bitwarden allows you to configure is the number of PBKDF2 iterations used on your master password. You can use this to strengthen your password’s security or increase performance on lower-end or older devices. By following the steps in this guide, you can configure your encryption key settings.

